Games

Welcome to the largest gaming community on Lemmy! Discussion for all kinds of games. Video games, tabletop games, card games etc.
Rules
1. Submissions have to be related to games
Video games, tabletop, or otherwise. Posts not related to games will be deleted.
This community is focused on games, of all kinds. Any news item or discussion should be related to gaming in some way.
2. No bigotry or harassment, be civil
No bigotry, hardline stance. Try not to get too heated when entering into a discussion or debate.
We are here to talk and discuss about one of our passions, not fight or be exposed to hate. Posts or responses that are hateful will be deleted to keep the atmosphere good. If repeatedly violated, not only will the comment be deleted but a ban will be handed out as well. We judge each case individually.
3. No excessive self-promotion
Try to keep it to 10% self-promotion / 90% other stuff in your post history.
This is to prevent people from posting for the sole purpose of promoting their own website or social media account.
4. Stay on-topic; no memes, funny videos, giveaways, reposts, or low-effort posts
This community is mostly for discussion and news. Remember to search for the thing you're submitting before posting to see if it's already been posted.
We want to keep the quality of posts high. Therefore, memes, funny videos, low-effort posts and reposts are not allowed. We prohibit giveaways because we cannot be sure that the person holding the giveaway will actually do what they promise.
5. Mark Spoilers and NSFW
Make sure to mark your stuff or it may be removed.
No one wants to be spoiled. Therefore, always mark spoilers. Similarly mark NSFW, in case anyone is browsing in a public space or at work.
6. No linking to piracy
Don't share it here, there are other places to find it. Discussion of piracy is fine.
We don't want us moderators or the admins of lemmy.world to get in trouble for linking to piracy. Therefore, any link to piracy will be removed. Discussion of it is of course allowed.
Authorized Regular Threads
Related communities
PM a mod to add your own
Video games
Generic
- !gaming@Lemmy.world: Our sister community, focused on PC and console gaming. Meme are allowed.
- !photomode@feddit.uk: For all your screenshots needs, to share your love for games graphics.
- !vgmusic@lemmy.world: A community to share your love for video games music
Help and suggestions
By platform
By type
- !AutomationGames@lemmy.zip
- !Incremental_Games@incremental.social
- !LifeSimulation@lemmy.world
- !CityBuilders@sh.itjust.works
- !CozyGames@Lemmy.world
- !CRPG@lemmy.world
- !OtomeGames@ani.social
- !Shmups@lemmus.org
- !VisualNovels@ani.social
By games
- !Baldurs_Gate_3@lemmy.world
- !Cities_Skylines@lemmy.world
- !CassetteBeasts@Lemmy.world
- !Fallout@lemmy.world
- !FinalFantasyXIV@lemmy.world
- !Minecraft@Lemmy.world
- !NoMansSky@lemmy.world
- !Palia@Lemmy.world
- !Pokemon@lemm.ee
- !Skyrim@lemmy.world
- !StardewValley@lemm.ee
- !Subnautica2@Lemmy.world
- !WorkersAndResources@lemmy.world
Language specific
- !JeuxVideo@jlai.lu: French
view the rest of the comments
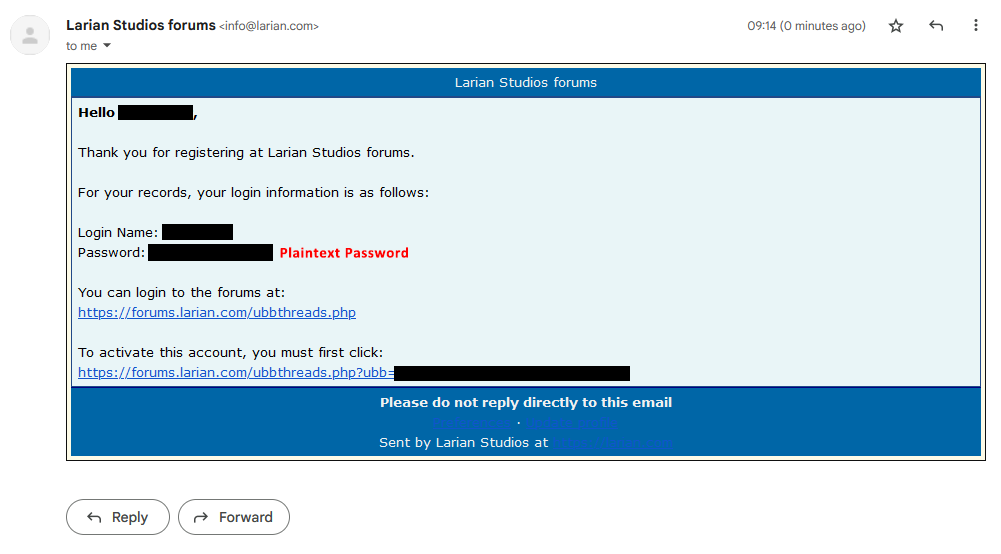
Yes, still not worth risking using a duplicate password though.
Honestly, why risk duplicate passwords even then? I have one strong password that I use for accessing my password manager, and let the password manager generate unique random passwords. Even if I had an easier password that I duplicated with some small changes, I'd still use a password manager to autofill it anyway. I use bitwarden personally, you can also self host it with vaultwarden but it seemed like more trouble than it was worth imo
This is a friendly reminder to everyone that password managers are not risk free either. LastPass was hacked last year, NortonLifeLock earlier this year.
Personally the risk of bitwarden is outweighed by its convenience (compared to self hosted/local only solutions) in my opinion, but I know that'll change real quick if bitwarden ever has a breach. If it does I'm jumping ship to a self hosted or local only solution, but I'm hoping that doesn't have to happen
Bitwarden is end to end encrypted. If the host gets hacked your passwords are still as safe as your master password is. Self hosting wouldn’t really be a huge help there. Possibly even detrimental depending on your level of competence at securing a public facing web host.
They're as safe as your master password is...and as the encryption is. LastPass famously got hacked recently, and in the aftermath of that many users noticed that their vault was encrypted using very small numbers of rounds of PBKDF2. The recommended number of rounds had increased, but LastPass left the number actually used too low for some users, rather than automatically increasing it. Users of Bitwarden and any other password vault should ensure that their vault is using the strongest encryption available.
Well, self-hosting makes you a smaller target. The most determined attackers are likely going to go after the biggest target, which is going to be a centralised service with thousands of users' vaults. If you host it yourself they probably won't even know it exists, so unless there's reason for someone to be specifically targeting you (e.g. you're a public figure), or you get hacked by some broad untargeted attack, you might be better off self-hosted from a purely security standpoint.
(That said, I still use centrally-hosted Bitwarden. The convenience is worth it to me.)
You’re underestimating the attack surface of a self hosted set up. You don’t need to be specifically targeted if, for instance, someone hacks the Bitwarden docker image you’re using, or slips a malicious link into a tutorial you’re reading. It’s not a set it and forget it solution either, you’re responsible for updating it, and the host OS. Like I said, depending on your competency, it’s not inherently more secure.
I heard people’s LastPass accounts were getting compromised after that theft, but I also don’t know how strong their master passwords were.
Yeah at this point it's considered likely that LastPass vaults are being cracked, based on LP being the common link between various other accounts that are being breeched.
A small number of rounds of encryption being the default for users with old enough accounts is believed to be a significant part of the issue. It means even if their password was a good one, the vault can be brute forced comparatively quickly.
If their password was actually good (18+ random characters) it's not feasible with current day technology to brute force, no matter how few PBKDF2 iterations were used.
Obviously it's still a big issue because in many cases people don't use strong enough passwords (and apparently LastPass stored some of the information in plaintext) but a strong password is still good protection provided the encryption algorithm doesn't have any known exploitable weaknesses.
Centralized, third party password managers, yes. Local-only managers like KeepassXC though, no concerns over some company getting hacked or cheeky
This is why I don't use a common centralized password manager, just like I don't use any of the most popular remote desktop solutions like TeamViewer for unattended access.
I run a consumer copy of Pleasant Password Manager out of AWS and use NoMachine for unattended access to any machines where I need it.
Security through obscurity is tried and true. Put as little of your security attack surface in the hands of others as is reasonable.
Applies to every site ever