Games

Welcome to the largest gaming community on Lemmy! Discussion for all kinds of games. Video games, tabletop games, card games etc.
Rules
1. Submissions have to be related to games
Video games, tabletop, or otherwise. Posts not related to games will be deleted.
This community is focused on games, of all kinds. Any news item or discussion should be related to gaming in some way.
2. No bigotry or harassment, be civil
No bigotry, hardline stance. Try not to get too heated when entering into a discussion or debate.
We are here to talk and discuss about one of our passions, not fight or be exposed to hate. Posts or responses that are hateful will be deleted to keep the atmosphere good. If repeatedly violated, not only will the comment be deleted but a ban will be handed out as well. We judge each case individually.
3. No excessive self-promotion
Try to keep it to 10% self-promotion / 90% other stuff in your post history.
This is to prevent people from posting for the sole purpose of promoting their own website or social media account.
4. Stay on-topic; no memes, funny videos, giveaways, reposts, or low-effort posts
This community is mostly for discussion and news. Remember to search for the thing you're submitting before posting to see if it's already been posted.
We want to keep the quality of posts high. Therefore, memes, funny videos, low-effort posts and reposts are not allowed. We prohibit giveaways because we cannot be sure that the person holding the giveaway will actually do what they promise.
5. Mark Spoilers and NSFW
Make sure to mark your stuff or it may be removed.
No one wants to be spoiled. Therefore, always mark spoilers. Similarly mark NSFW, in case anyone is browsing in a public space or at work.
6. No linking to piracy
Don't share it here, there are other places to find it. Discussion of piracy is fine.
We don't want us moderators or the admins of lemmy.world to get in trouble for linking to piracy. Therefore, any link to piracy will be removed. Discussion of it is of course allowed.
Authorized Regular Threads
Related communities
PM a mod to add your own
Video games
Generic
- !gaming@Lemmy.world: Our sister community, focused on PC and console gaming. Meme are allowed.
- !photomode@feddit.uk: For all your screenshots needs, to share your love for games graphics.
- !vgmusic@lemmy.world: A community to share your love for video games music
Help and suggestions
By platform
By type
- !AutomationGames@lemmy.zip
- !Incremental_Games@incremental.social
- !LifeSimulation@lemmy.world
- !CityBuilders@sh.itjust.works
- !CozyGames@Lemmy.world
- !CRPG@lemmy.world
- !OtomeGames@ani.social
- !Shmups@lemmus.org
- !VisualNovels@ani.social
By games
- !Baldurs_Gate_3@lemmy.world
- !Cities_Skylines@lemmy.world
- !CassetteBeasts@Lemmy.world
- !Fallout@lemmy.world
- !FinalFantasyXIV@lemmy.world
- !Minecraft@Lemmy.world
- !NoMansSky@lemmy.world
- !Palia@Lemmy.world
- !Pokemon@lemm.ee
- !Skyrim@lemmy.world
- !StardewValley@lemm.ee
- !Subnautica2@Lemmy.world
- !WorkersAndResources@lemmy.world
Language specific
- !JeuxVideo@jlai.lu: French
view the rest of the comments
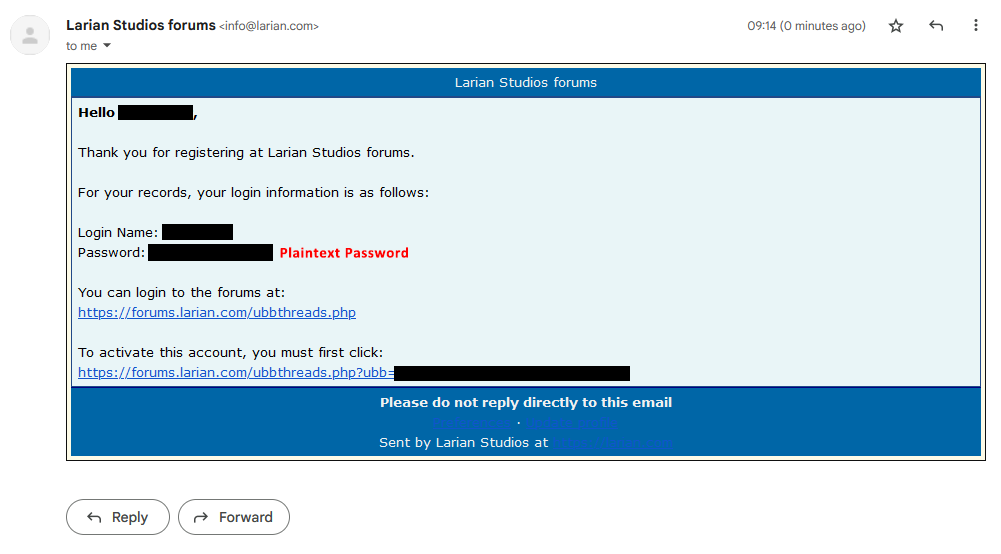
no, they probably dont.
they just send it to your email upon registration, which is kinda a bad idea, but they are probably storing passwords hashed afterwards.
...and if they keep the emails they send out archived (which would be reasonable), they also have it stored in plaintext there.
Automatically generated emails usually don't get saved.
As the designated email dev at my company I can confidently say this is not true.
Not saying that this specific email is persisted, but almost all that I work with are. It's a very common practice.
Yeah, we save most emails sent out at my work.
I wonder how much this varies depending on the amount of data it would require to store the emails of a company. I know nothing about this subject, but does it occur where companies with very large email lists would forgo storing those types of emails to save data costs?
In my experience it varies a lot. Even in our own system certain emails are stored differently. There are a few "we legally have to deliver this email and might need to prove it later" notifications. We store a PDF of those in s3. For others we might just save the data, a sent timestamp, and a key for which email visual template was used.
I also thought of a counter argument to my point overnight. We don't store one super duper high volume email which is the email that only has an MFA code. We would also absolutely never ever dream about allowing a plaintext password in an email, so we're probably following different patterns in the first place.
So it's in plaintext in their email system
these emails don't usually get copied to local outbox folder (as any oher auto generated emails)
password may end up in cache somewhere tho....
and this is why it's a bad idea and rarely done nowadays
Generated emails usually don't get saved, as soon as it is delivered it will be gone.
I've literally never had a service provider email me my own password ever. Maybe a OTP, but never my actual password. And especially not in plaintext.
What would be the necessity behind emailing someone their own password? Doesn't that defeat the purpose of having a password? Email isn't secure.
I find that very hard to believe. While it is less common nowadays, many, if not most, mailing list and forum software sent passwords in plaintext in emails.
A lot of cottage industry web apps also did the same.
They're probably just young.
Idk if I'm misremembering, but it's my impression that they did this a lot in the 2000s, haha. I guess bad practices have a habit of sticking around
I've had service providers physically mail my own password to me before. Just crazy.
Always use unique passwords for every site.
"Kinda a bad idea?" This is fucking insane.
Is it though? While it certainly isn't something I'd recommend, and I've encountered it before, if E2E encryption exists we cannot assume a data exposure had occurred.
What they do on the backend has nothing to do with this notification system. Think of it as one of these credentialess authentication systems that send a 'magic link' to your inbox.
this is still a terrible idea. the system should never know the plaintext password.
logs capture a lot even automated emails. i don't see a single reason to send the user their plaintext password and many reasons why they shouldn't
passwords are usually hashed server-side tho and that's done for a reason.
if handling passwords correctly, server side hashing is way more secure then client-side. (with client side hashing, hash becomes the password...)
But that still means they had your plaintext password at some point.
Edit: which, as some replies suggest, may not actually be much of an issue.
I'm still skeptical about them returning it, however.
hashing on client side is considered a bad idea and almost never done.
you actually send your password "in plain text" every time you sign up.
Really everytime you log in too.
It's not a bad idea and it is often done, just not in a browser/webapp context.
Can you give an example where this is done?
Sorry, I should have included an example in my comment to clarify, but I was in a rush.
HMAC is a widely used technique relies on hashing of a shared secret for verifying authenticity and integrity of a message, for example.
Of course. You receive the password in plain on account creation, do the process you need, and then store it hashed.
That's fine and normal
When you create an account you type your password in. This gets sent to the server, and then it is hashed and stored
So there is a period of time where they have your unhashed password
This is true of every website you have ever made a password on
I've never even heard of the game studio I'm not defending them, I was replying to the person who said the company should never have your unhashed password, and explaining that they have to at some point in the process
So why would an agent at Larian have man-in-the-middle access between the password being sent to the server, and the auto-hash?
Um. Yeah, because you provided it to them. They have to have it in plain text in order to hash it.